Editor of security solutions, Eset has discovered a new type of malware that is hidden in fake applications on Android. Very sophisticated, this virus thwarts the protection by double authentication to intercept the passwords and codes received by SMS.
For better security, many web services provide two-step authentication with a mobile phone number, a method that sends an SMS to the user with a one-time code to enter in addition to his or her usual password when he identifies himself on the site.
This adds extra security since an attacker can not access the account only by stealing the password. There are different ways for hackers to bypass this feature. One is social engineering, where a scammer contacts the mobile operator’s customer service by pretending to be the victim, in order to transfer the line, and thus to receive the SMS containing the code.
Another method was to infect the victim’s mobile with an application to read the SMS. However, Google, publisher of Android, cleaned up last March by limiting the application access to SMS and removing applications from the Play Store who requested authorization without being able to justify it. This put an end to programs that were nothing other than malware intended to intercept two-step authentication verification codes. Unfortunately, the respite was short-lived.
Notifications display SMS content
The anti-virus editor Eset has discovered new applications that have put in place an ingenious way to circumvent the restrictions created by Google. In a post published on his blog, the firm detailed the process used by this new malware dubbed Android / FakeApp.KP. Rather than accessing SMS directly from the device, these applications simply asked for access to notifications.
When receiving an SMS, its content is displayed as a notification on the smartphone and can be intercepted by the malware. This technique even offers an advantage over direct access to SMS, since it also works with some two-step authentication systems that send the single-use code by e-mail, which also appears as a notification.
However, the method has a limit, since it only has access to the truncated text displayed in the notification, and not to the full content of the messages. For an SMS this is enough, but for the emails, the malware has access to the code, only if it is included at the beginning of the message.
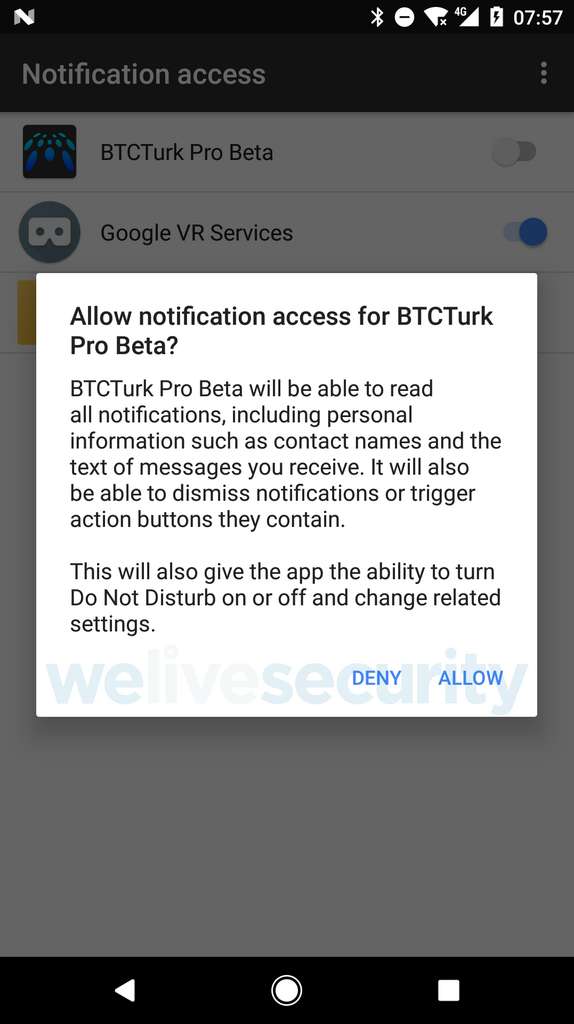
Only a cryptocurrency exchange site is targeted for the moment
To date, these applications target the Turkish cryptocurrency exchange site BtcTurk. By masquerading as a legitimate application for the service, the malware manages to trap the user who then enters his credentials. The crooks get the password and the one-time code to access the victim’s account.
In order to prevent the victim from realizing that the application is fraudulent and does not offer any real access, it displays an error message after entering the identifiers, indicating that the mobile application is currently out of service because of a change in the SMS verification system. The malware can then silently wipe the smartphone and delete any new notification so that the victim is not informed of fraudulent transactions on his account via e-mail, SMS or another application.