Experts in cybersecurity have discovered a flaw in SIM cards that allows you to take control of a smartphone remotely. One billion phones are affected by this breach.
AdaptiveMobile Security, a global leader in mobile network security, has released details of a new vulnerability that potentially affects more than one billion phones. A simple SMS is enough to take control of a device and can track the victims. The researchers named it Simjacker, and indicate that they have already seen a number of practical cases. According to the researchers, the fault has been exploited by a company that works with governments to monitor individuals.
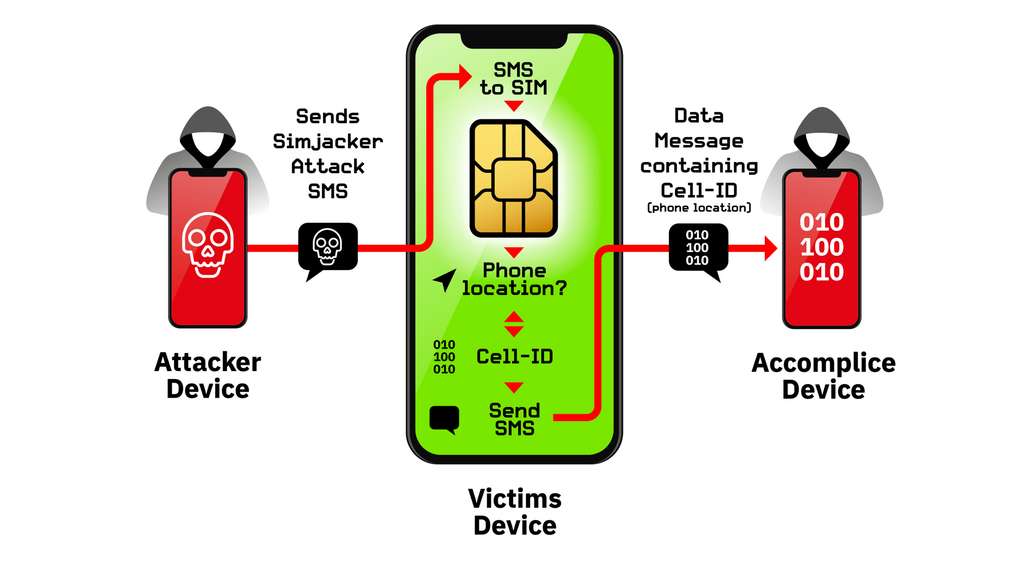
By sending an SMS containing a specific code to a mobile phone, the SIM card receives instructions for taking control of the device and executing certain commands or retrieving data. The attack uses the software contained in the SIM card called “S @ T Browser”, which is able to interact with the mobile to retrieve information.
SMS attack completely invisible to the victim
In the main attack discovered by the researchers, the mobile of the victim receives an SMS designed not to trigger a notification. The system retrieves the IMEI number of the device, as well as information about the base station to which it is connected, and sends the data to another SMS.
The SMS are not visible at any time for the victim, leaving no trace in the inboxes or sending the mobile. By identifying the base station, the SMS author can locate an individual with increasing accuracy, the denser the mesh of the relay antennas. Location data is therefore much more accurate in the city than in the countryside.
The “S @ T Browser” is quite old, has not been updated since 2009, and can be found in most SIM cards, including eSIMs. It is intended in particular to add features like consulting its bank balance via its SIM card. It is used by operators in more than 30 countries, representing a potential market of nearly one billion people. The functions that can be exploited remotely are not limited to the location of the device since the attacker can call on a complete list of STK commands. The researchers were able to open the browser, make calls, send messages.
A system that could be exploited by many criminal groups
Researchers have confirmed that vulnerability is currently being exploited very actively. ” In one country we see about 100-150 specific mobile numbers targeted daily by Simjacker attacks, with peaks of 300 numbers in one day.
In addition, this system could send messages to victims containing false information, call surcharged numbers, act as a spy system via the microphone by calling a specific number, install malware via the browser, retrieve other information about the device or simply disable the SIM card completely to block the mobile.
The researchers shared their findings with the GSM Association and SIM alliance organizations to alert operators and improve the security of new SIM cards. In the meantime, operators will have to analyze messages to block suspicious SMS. They could also change the security settings of SIM cards and uninstall the “S @ T Browser” remotely, but the operation may be quite difficult and time-consuming.